In early May 2025, a hacker going by the alias “ByteBreaker” shook the cybersecurity community by claiming to have leaked personal data from over 1.2 billion Facebook users. The alleged breach instantly sparked a wave of media coverage, panic, and speculation. But was it truly a fresh breach — or just another case of old data repackaged?
As a cybersecurity platform focused on truth, The Cyber Monk breaks down what’s real, what’s not, and why you should still care.
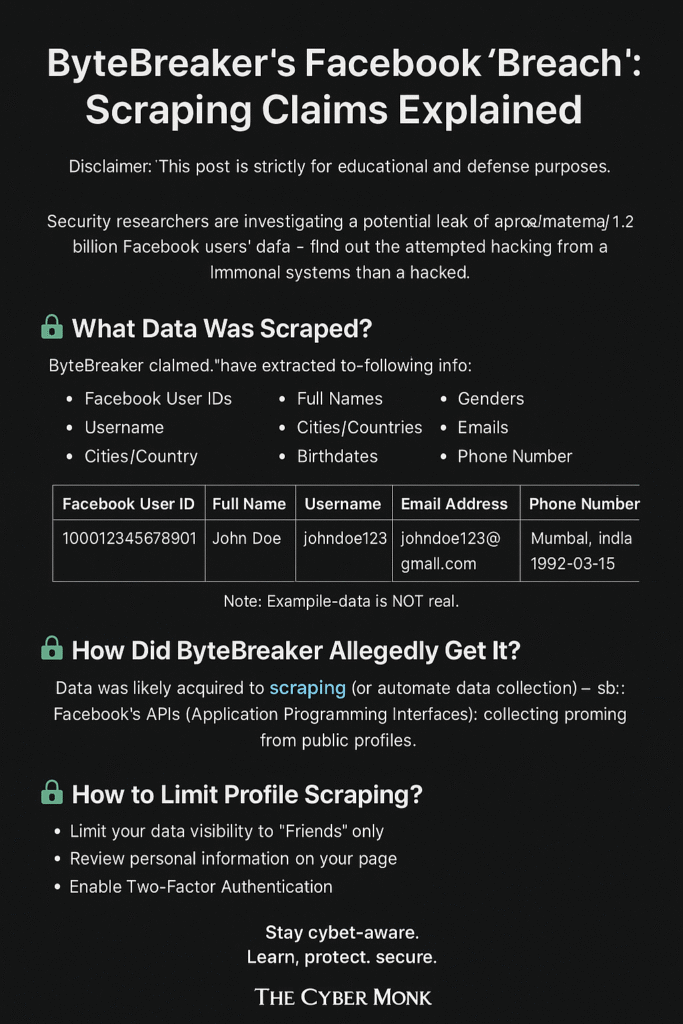
🔍 What Was Allegedly Leaked?
ByteBreaker claimed the following personal data of Facebook users was exposed:
- Full names
- Email addresses
- Phone numbers
- Facebook usernames
- Gender and location
- Facebook user IDs
A sample of 100,000 users was shared publicly for verification purposes — which prompted several research outlets to investigate.
✅ Was It Legit?
- Cybernews researchers analyzed the sample and concluded the data “appears to be legitimate” based on matching real identities.
- However, no proof has surfaced that this is new data.
- Many cybersecurity experts, including from Hackread, believe the data was:
- Scraped from public Facebook profiles, not stolen via a vulnerability.
- Possibly recycled from older Facebook leaks, such as the massive 2021 Facebook breach.
🛑 Meta’s (Facebook) Response
Meta (Facebook’s parent company) has denied any new security breach, stating:
“This dataset is consistent with information that was previously scraped and made public in 2021.”
Meta emphasized that no internal systems were breached and reiterated the importance of users limiting what they share publicly.
🧠 Hacking vs. Scraping — What’s the Difference?
| Hacking | Scraping |
|---|---|
| Exploits vulnerabilities or flaws | Uses bots to collect public data |
| Illegal, and causes data breaches | Often legal, depending on usage |
| Requires system access | Requires only visible public data |
ByteBreaker didn’t hack Facebook. The data was likely collected using automated scripts that scraped publicly visible profile details — a practice that Facebook has battled for years.
🚩 Red Flags Around ByteBreaker
- The hacker’s forum profiles were deleted.
- Their contact information kept changing.
- They couldn’t prove the data was fresh or uniquely obtained.
- Some of the leaked data matches previously leaked Facebook data.
This pattern suggests that ByteBreaker may be seeking attention, money, or both, rather than exposing a real vulnerability.
🔐 What Should Users Do?
Even if the data isn’t freshly stolen, it’s still real data — and can be misused for:
- Phishing emails & SMS attacks
- Social engineering
- SIM swapping
- Credential stuffing (if old passwords are reused)
✅ Recommended Actions:
- Review and tighten your Facebook privacy settings
- Hide your email and phone number from the public
- Enable two-factor authentication (2FA)
- Use unique passwords for each service
📊 Infographic: Understanding the ByteBreaker Leak
💬 Final Verdict
The ByteBreaker leak is most likely not a new breach, but a resurfacing of public and previously leaked data — dressed up to look fresh. But that doesn’t mean it’s harmless.
“Even scraped or outdated data, when put in the wrong hands, can fuel phishing scams, identity fraud, and other cyberattacks.”
— The Cyber Monk Team
In the age of open information, what you share online matters more than ever. Stay private, stay vigilant.











Leave a Reply